How Sophisticated Fraudsters Are Targeting Accounts Payable Teams
Email scams have grown increasingly sophisticated—and costly. One of the most alarming trends in cybercrime today is the rise of targeted invoice scams, in which fraudsters impersonate company executives and vendors to deceive employees into making bogus payments. These scams aren’t just general phishing attempts—they’re tailored, strategic, and exploit your company’s internal dynamics.
A recent example shared with us is a textbook case of how convincing these scams can be. In it, a scammer poses as a company owner and initiates a thread with the person responsible for accounts payable. The goal was to trick them into wiring nearly $10,000 to a fake vendor. The scam is slick, believable, and—if not caught in time—potentially devastating.
Let’s break down how this scam works, how to spot it, and how your business can protect itself.
What Is a Targeted Invoice Scam?
Also known as business email compromise (BEC) or executive impersonation scams, these frauds occur when cybercriminals spoof or compromise email accounts to impersonate someone within the organization, typically a CEO, CFO, or department head. They then email someone in the accounts department (often by name), urgently requesting payment for a seemingly legitimate invoice.
In the case we reviewed, the scammer spoofed a conversation between “K Rice,” an executive, and “Amanda,” who manages payments. The email pressured Amanda to pay an “outstanding ZoomInfo invoice” totaling $9,830, referencing what appeared to be a renewal for a software subscription. A fraudulent contact was even cc’d as the supposed billing representative.
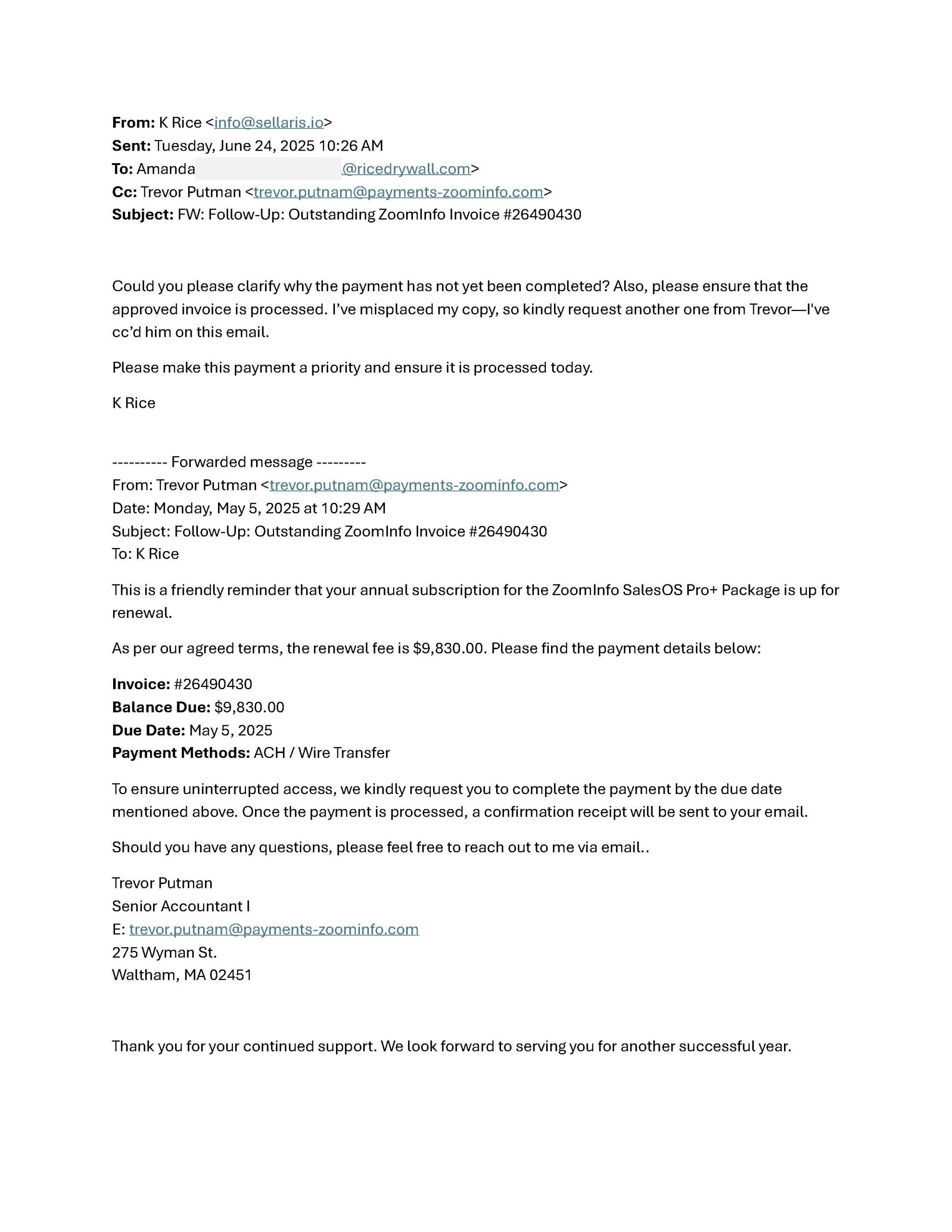
This type of setup utilizes authority, urgency, and insider knowledge to overcome doubt and facilitate the transaction.
Why These Scams Are So Convincing
Unlike broad spam emails with typos and obvious scams, targeted invoice scams are convincing for several reasons:
They Use Real Names and Roles
Scammers research the company—often through LinkedIn, company websites, or leaked data—and identify key players. In the example, they knew Amanda handles invoices, and they used the name of a real executive, K Rice, to simulate a legitimate request.
Spoofed or Similar Email Addresses
Fraudsters often use addresses that closely resemble legitimate ones (e.g., info@sellaris.io or payments-zoominfo.com), making them easy to overlook in a busy inbox.
Thread Hijacking or Fabricated Threads
By spoofing a forward or reply chain, the scammer creates the illusion of a prior conversation and thereby appears more legitimate. The “forwarded” message in this example conveyed a sense of a follow-up, thereby increasing pressure on the recipient.
Urgency and Authority
The email demands that the payment be made today and even states that the invoice has been approved. This discourages second-guessing and bypasses regular payment review protocols.
Red Flags to Watch For
Even well-trained employees can be caught off guard, but there are common signs to watch out for:
- Unusual Email Addresses: Always double-check the domain. Legitimate vendors typically use official domains (e.g., @zoominfo.com, not @payments-zoominfo.com).
- Unexpected or Rushed Payment Requests: If a payment request appears out of the blue and requests same-day payment, pause and verify.
- Emails That Bypass Your Regular Workflow: If an invoice skips your usual approval process or comes via an unexpected chain of command, question it.
- Poor Formatting or Slightly Off Language: Many scams still carry subtle grammatical or stylistic oddities, though they’re getting better at this.
How to Protect Your Business
Use Email Authentication Tools
Implement SPF, DKIM, and DMARC records to prevent spoofing of your company’s domain. These tools help email servers verify whether a message truly came from your organization.
Train Your Staff Regularly
Employees at every level—especially those in finance—should receive ongoing training on how to spot and report suspicious emails. Include mock phishing exercises to test awareness.
Verify Before You Pay
Always confirm payment requests, especially if they’re large, urgent, or new. Use known contact methods—not the email in the message. A quick phone call can prevent disaster.
Establish Dual Authorization for Payments
Require at least two people to review and approve any payment above a certain amount. This simple rule can dramatically reduce risk.
Keep Your Team Informed
Encourage open communication. If someone receives a strange or pressuring email—even from a familiar name—they should feel empowered to report it.
Limit Public Exposure of Job Roles
Consider how much detail about your org chart you’re putting online. The less scammers know about who handles what, the harder it is for them to tailor their attacks.
What to Do If You Suspect a Scam
If someone in your company receives an email like the one in the example:
- Do Not Reply or Click Any Links
- Report It Immediately to Your IT or Security Team
- Verify with the Supposed Sender by Phone
- Flag the Email as Phishing in Your Email Platform
- Notify Your Bank if a Payment Has Been Made
Swift action can sometimes recover funds or assist law enforcement in tracking the scammers.
Real-World Impact
The FBI estimates that business email compromise scams have cost companies over $50 billion globally since 2013. Even small companies are being hit, many with five-figure losses they can’t afford to absorb. The scam targeting Amanda could have cost her company nearly $10,000 for nothing but a few well-placed emails.
Final Thoughts
Email scams like these are a sobering reminder that cybersecurity is not just an IT issue—it’s a business issue. The good news is that with awareness, training, and clear protocols, you can reduce your vulnerability and stay ahead of scammers.
If you found this post helpful, share it with your finance and operations teams, and consider adding scam simulations to your next cybersecurity training. The next bogus invoice could be in your inbox right now.

